Advanced Penetration Testing: Real-World Insights for Modern Cyber Defenders.
Advanced Penetration Testing (APT) is a method of simulating cyber attacks on an organization’s computer systems and networks to assess their defenses.
Digital AI World Hackers are getting smarter every day, and simple security scans aren’t enough to stop them. That’s why many businesses now use advanced penetration testing.
APT involves using various techniques, including social engineering, network scanning, and exploit development, to bypass security controls and gain unauthorized access. The goal of APT is to identify vulnerabilities and provide recommendations for remediation, helping organizations to improve their overall security posture and reduce the risk of a real-world attack.
APT is typically performed by trained security professionals with the permission of the organization’s leadership.
Today, AI and cloud security are big parts of testing too, along with new risks from IoT devices.
To stay safe, it’s important to follow best practices: get permission, define your scope, protect data, and meet rules like GDPR or HIPAA.
Advanced penetration testing gives you a real look at how strong your defenses are before real hackers try.
Advanced penetration testing (APT) goes beyond basic vulnerability scanning to simulate sophisticated attacks, often targeting high-security environments.
It involves techniques like custom exploit development, advanced evasion tactics, and post-exploitation activities like lateral movement and privilege escalation. These techniques aim to identify and exploit complex vulnerabilities that traditional methods might miss.
Advanced Penetration Testing Fact: Uncovering Vulnerabilities
Penetration testing, also known as pen testing, is a simulated cyber attack against a computer system, network, or web application to assess its security vulnerabilities. Advanced penetration testing involves sophisticated techniques and tools to mimic real-world attacks.
APT type of testing helps organizations identify and prioritize vulnerabilities, evaluate the effectiveness of their security controls, and develop strategies to improve their defenses.
Here’s a more detailed look at advanced penetration testing facts and key characteristics of APT:
Customization and Tailoring: Techniques are tailored to specific target environments, including developing custom exploits for unique vulnerabilities.
Evasion and Stealth: Advanced obfuscation techniques and mimicking legitimate traffic patterns are used to avoid detection by security systems.
Chaining and Pivoting: Multiple vulnerabilities are combined to create a larger attack surface, and compromised systems are leveraged to access deeper network segments.
Automation and Scalability: AI and machine learning are used to automate testing and scale assessments efficiently.
Post-Exploitation Focus: Emphasis is placed on lateral movement within a network and privilege escalation to access sensitive information.
Advanced Penetration Testing Techniques And Examples
Web Application Penetration Testing: Advanced web application testing goes beyond basic checks, looking for sophisticated vulnerabilities like zero-day exploits and Server-Side Request Forgery (SSRF).
Network Segmentation Testing: Pen-testers simulate post-exploitation tactics to identify weaknesses in network segmentation and access controls.
API Penetration Testing: With the increasing use of APIs, penetration testing ensures they are secure against common threats like API key leaks and injection attacks.
Why is Advanced Penetration Testing (API) Fact Important?
Penetration testing (or VAPT) is a security exercise in which experts attempt to find vulnerabilities in a computer system. It helps to identify any weak spots in a system’s defenses that hackers could attack. More simply, companies hire a friendly “ethical hacker” to break into your systems.
Identifies Complex Vulnerabilities: Advanced techniques help uncover vulnerabilities that might be missed by traditional methods.
Simulates Real-World Attacks: By simulating advanced attacks, organizations can assess their resilience against sophisticated threats.
Supports Incident Response: Pen-testing helps evaluate the effectiveness of incident response plans and identify areas for improvement.
Enhances Security Posture: By proactively identifying vulnerabilities and weaknesses, security teams can strengthen defenses and prevent data breaches.
What Sets Apart Basics From Advanced Pen-Testing?
Basic security testing often checks for known problems, like weak passwords or outdated software. It’s helpful, but it only looks at the surface. Advanced penetration testing goes much deeper. It acts like a real hacker, trying to break in using smart methods and hidden paths. It doesn’t just scan for issues, it tries to exploit them, see how far it can go, and show the real damage a hacker could cause.
There are different ways to do this kind of testing. In a black-box test, the tester knows nothing about your system, just like a real attacker. A white-box test gives the tester full access to see inside. A gray-box test is somewhere in between.
Some companies also choose blind or double-blind testing, where the team being tested doesn’t know it’s happening, so it checks how well they can respond in real time.
Advanced testing is not only about finding flaws, it helps teams learn how to fix them, fast. It also shows how strong your defenses are if an attacker gets past the first layer. Advanced facts of penetration testing are a part of businesses that handle private data, work in the cloud, or use IoT devices, often rely on advanced tests to stay safe.
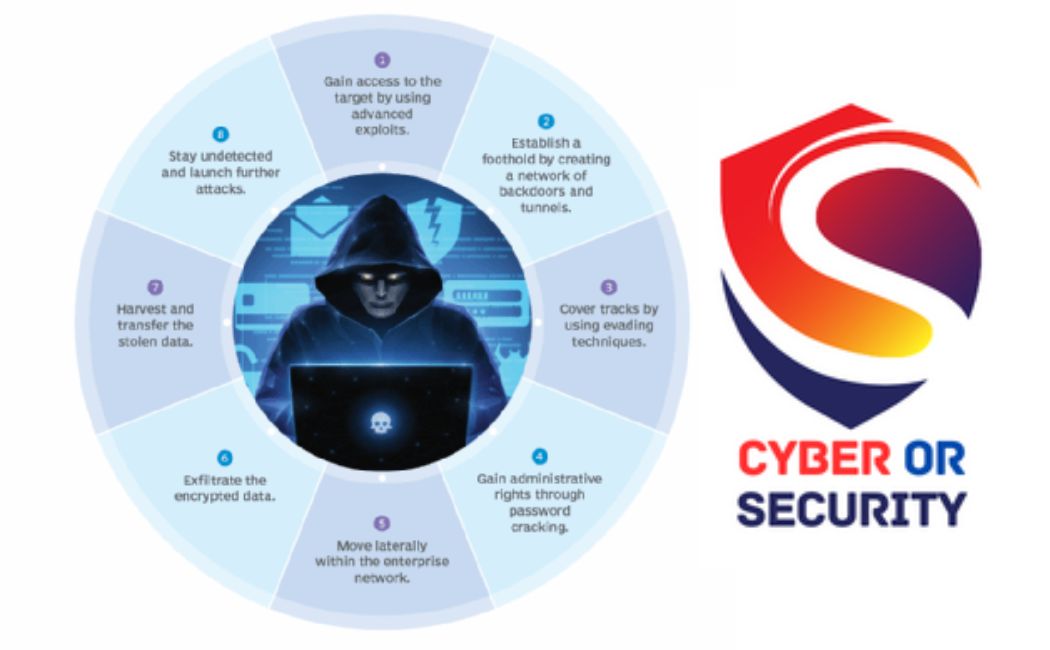
What Are the 5 Stages of Advanced Penetration Testing?
Advanced penetration testing doesn’t happen all at once. It follows a step-by-step process to safely and clearly show how hackers could break into a system and how to stop them. Each phase has a purpose, and together, they give a full picture of your security.
1. What Is Reconnaissance (Information Gathering)?
Information Gathering is the first step, also called “recon.” The tester collects as much information as possible about the target without touching the system directly.
Example: A tester might look up your company’s domain names, email addresses, employee social media, and past data leaks, all from public sources. This helps build a picture of possible weak spots.
2. How Does Scanning Work in Penetration Testing?
After gathering information, the tester scans your systems to find open ports, running services, and software versions.
Example: Using tools like Nmap or Nessus, they might find that your server runs an old version of WordPress, which is known to have security bugs. Scanning can be active, interacting with the system, or passive, watching network traffic quietly.
3. What Happens During Exploitation?
This is when the tester tries to break in by using the weaknesses they found. It’s like opening a locked door using a stolen key.
As Like, they might use Metasploit to exploit a bug in your login page, or run SQLmap to pull sensitive data from your database. This is the most exciting. But also a risky part, so it’s always done under strict rules and with permission.
4. Why Is Post-Exploitation Important?
Once inside, the tester explores how much damage a real attacker could do. This phase shows how deep the problem goes.
Example: If they get access to one employee account, can they move around the network and steal customer data? Or take over the whole system? Tools like BloodHound help testers map out systems like Active Directory, where one small access point might lead to full control.
5. What’s The Final Report: Advanced Facts Of Penetration Testing?
After testing is done, the tester creates a report with all the findings. It explains what was found, what it means, and how to fix it.
Example: The report might say, “Your admin login is vulnerable to brute-force attacks. So, recommend enabling two-factor authentication. The report usually has two parts: a simple version for managers and a detailed version for the technical team.
However, each phase builds on the one before it. Together, they show where your defenses are weak, how an attacker might break in, and what to fix first. That’s why following this full process, not just scanning, is key to advanced penetration testing.
What Are the Must-Have Tools for Advanced Penetration Testing?
Advanced penetration testing requires the right mix of tools. These tools help ethical hackers safely explore systems, find weaknesses, and test how far an attacker could go, without causing real harm.
You can’t run a strong penetration test without the right tools. These tools help testers scan, attack, bypass defenses, and report findings just like a hacker would, but in a legal and controlled way. Some are free and open-source, while others are paid and more advanced.
Below are the most popular and powerful tools used by ethical hackers today. Let’s take a closer look at the most widely used tools in the field, with real-world examples for each.
1. Nmap: How Do You Discover What’s Running on a Network?
Use: Network mapping and port scanning
Why it matters: You can’t protect what you can’t see. Nmap, “Network Mapper,” shows testers which devices are active, what ports are open, and what services or software are running.
Real Example: A tester runs nmap -sV 192.168.1.10 and finds that port 21 (FTP) is open on a server running an outdated version of vsFTPd. This alerts them to a potential vulnerability from a known exploit, such as an unauthenticated backdoor.
Nmap is often the first tool used in any test, it helps map the battlefield before launching further analysis.
2. Burp Suite Pro: How Do You Break Into Web Apps Safely?
Use: Web application testing and vulnerability detection
Why it matters: Websites are often the easiest way for hackers to get in. Burp Suite Pro acts as a “middleman” between your browser and the website, letting testers capture and modify web traffic in real time.
Real Example: A tester intercepts a password reset request using Burp. They see that the system doesn’t verify the user before resetting the password. This allows them to reset someone else’s password without permission, a critical flaw.
Burp also automates scanning for common bugs like XSS, CSRF, and insecure cookies, things often missed in manual code reviews.
3. Metasploit: Can You Test Real-World Exploits Without Causing Harm?
Use: Exploitation and payload delivery
Why it matters: Once vulnerabilities are found, testers need to know what an attacker could actually do. Metasploit is a powerful tool that safely runs known exploits against systems to see if they’re still vulnerable.
Real Example: A tester uses Metasploit to exploit an unpatched Windows 7 machine using the EternalBlue vulnerability. They gain remote code execution and install a meterpreter shell, a stealthy, command-line backdoor to explore the system further.
Metasploit also helps with post-exploitation, like pivoting to other machines, to show how one weak system can lead to a full breach.
4. SQLmap: Can You Steal or Alter Data from a Web Form?
Why it matters: Many websites talk to databases, and if those databases are poorly protected, attackers can steal information, delete data, or even gain admin access. SQLmap automates this kind of attack.
Real Example: A tester targets a search box on a website with SQLmap. The tool finds that it is vulnerable to blind SQL injection and is able to extract usernames and password hashes from the database, all without logging in.
Even today, SQL injection is one of the most common and dangerous web vulnerabilities.
5. BloodHound: How Can Hackers Take Over from the Inside?
Use: Active Directory attack mapping
Why it matters: Inside a company’s network, many systems run on Active Directory, Microsoft’s user and permission management system. BloodHound shows how seemingly harmless user permissions can be chained together to give attackers full control.
Real Example: A tester uses BloodHound to map internal user relationships. They find that a junior employee has permission to reset passwords for a group with domain admin rights, a major misconfiguration that could lead to full domain takeover.
BloodHound visualizes this as a graph, making it easy to understand how small issues add up to big risks.
6. Kali Linux & Parrot OS: Why Do Hackers Use Special Operating Systems?
Use: All-in-one penetration testing platforms
Why it matters: Most testers use a special Linux system built just for ethical hacking.
Kali Linux and Parrot OS come pre-loaded with hundreds of tools, saving time and effort.
Real Example: A tester boots Kali Linux on a laptop, connects it to a test network, and instantly has access to tools like Nmap, Burp, Hydra, Nikto, and more ready to use from the terminal or desktop.
These OSes are updated often and used in professional certifications like OSCP, CEH, and CPT, making them industry standards.
So, having the right tools is only half the game; knowing how and when to use them matters more. Advanced penetration testing brings all these tools together into a planned, controlled, and legal process that shows how strong your defenses truly are.
Supported Article: Exploring the Impact of What Mean Standard Penetration Testing?
How Is Penetration Testing Different from Ethical Hacking?
These two terms often get mixed up, and that’s understandable. Both deal with finding and fixing security issues before real hackers can attack. But they’re not exactly the same. Let’s break it down simply so you can see how they connect and what sets them apart.
1. What Is Ethical Hacking?
Ethical hacking is a broad term. It means any legal hacking done with permission to improve security. It can include many activities: vulnerability scanning, social engineering, password cracking, phishing simulations, wireless network testing, and even physical security checks.
However, an ethical hacker might try to sneak into your office building or send a fake email to employees to see if they click a dangerous link. They follow a strong code of ethics, always get permission first, and report all findings responsibly.
2. What Is Penetration Testing?
Penetration testing is a specific type of ethical hacking. It focuses more on finding real ways to break into a system, just like a hacker would. Penetration testers don’t just find weaknesses; they try to exploit them to see what could happen in a real attack.
So, a penetration tester may find a weak admin password on your web server, use it to log in, and then try to access sensitive customer data, all to show how much damage a real attacker could do. Penetration testing is usually structured, follows a step-by-step process, and ends with a clear report. It’s often done at regular intervals or after big changes to your system.
3. What’s the Main Difference between Ethical Hacking And Penetration Testing?
| Facts | Ethical Hacking | Penetration Testing |
| Purpose | Broad security improvement | Deep testing of real-world attacks |
| Scope | Can include many types of tests | Focused on active exploitation |
| Method | May or may not follow a fixed structure | Follows defined phases (recon to report) |
| Output | General insights and suggestions | Proof-based report with detailed fixes |
Think of ethical hacking as the umbrella. Penetration testing is one of the most important parts, as it is more focused, more technical, and often used when businesses need real answers fast.
Why Does Penetration Testing Matter to Your Business?
If you’re a business owner or IT decision-maker, knowing the difference helps you choose the right service. If you want to check everything from employee habits to firewalls, hire an ethical hacker
If you want to know how far a real attack could go, ask for a penetration test. Both are important, but the penetration test gives the most realistic picture of what’s at risk and how to stop it.
Where Is Advanced Penetration Testing Used in the Real World?
Penetration testing isn’t just for large tech companies. Today, every industry that handles data, money, or users relies on it to stay safe. Let’s explore how different sectors use advanced penetration testing and what real risks they’re trying to avoid.
1. Healthcare: Can Patient Data Be Stolen?
Healthcare providers collect highly sensitive information like medical histories, prescriptions, and billing records. A data breach here isn’t just a tech issue it can risk lives or violate strict regulations like HIPAA.
Example: A tester checks if hospital web portals are vulnerable to SQL injection. They find a flaw that allows access to patient names and diagnosis reports, a serious privacy risk.
Why it matters: Medical devices and record systems are often outdated and connected to wider networks, making them easy targets.
2. Finance: Can Hackers Break the Bank?
Banks, fintech apps, and online payment systems are frequent targets for cybercriminals. A successful attack can lead to millions in fraud or stolen identities.
Example: A tester simulates an attack on a banking app’s login system. By bypassing authentication, they gain access to transaction history and stored card details.
Why it matters: Financial organizations are often required to undergo regular PCI-DSS compliance testing, where penetration testing plays a key role.
3. Cloud Environments: Are Virtual Systems Secure Enough?
As more companies move to cloud platforms like AWS, Azure, or Google Cloud, cloud penetration testing becomes critical. Misconfigured storage buckets or leaked API keys can expose huge amounts of data.
Example: A tester finds that a cloud storage bucket holding internal documents is set to “public” by mistake. Anyone on the internet could access it without logging.
Why it matters: Cloud setups are complex, and small mistakes can lead to big data leaks.
4. Corporate Networks: Can Hackers Get Inside from the Outside?
Even small companies have internal networks, shared drives, and admin portals. These systems often hold private files, employee data, and business secrets.
Example: A tester uses phishing to trick an employee into clicking a fake link. This gives them remote access to the network, where they use BloodHound to escalate to full admin rights.
Why it matters: Internal threats and social engineering are still the most common way attackers break in.
5. Software & SaaS: What If Your Product Gets Compromised?
Companies that build software or apps must protect both their platform and their users. A vulnerability in the product can damage brand trust and lead to mass compromise.
Example: A SaaS tester uses Burp Suite to find a Cross-Site Scripting (XSS) flaw in a user comment field. If exploited, this could be used to steal user sessions or take over accounts.
Why it matters: Regular penetration testing helps maintain product integrity and meet customer security expectations.
However, Penetration testing is used wherever security matters, and that’s almost everywhere today. From hospitals to banks to startups, it gives organizations the evidence they need to fix weak points before attackers exploit them.
What Are the Emerging Trends in Penetration Testing for 2025?
As cyber threats grow smarter, penetration testing is evolving fast. The traditional “manual-only” approach is no longer enough. Let’s look at the new trends shaping the future of ethical hacking and how organizations are staying ahead in 2025.
1. AI-Powered Penetration Testing: Can Machines Hack Smarter Than Humans?
Artificial Intelligence (AI) and machine learning are changing the way penetration tests work. These tools can now automatically find weaknesses, analyze patterns, and even simulate advanced attacks faster than human testers. AI tools like Pentera or SnapAttack can scan entire networks, detect misconfigurations, and simulate ransomware attacks in minutes, something that used to take days.
Why it matters: AI speeds up the testing process, reduces human error, and allows businesses to run continuous security checks not just once or twice a year.
2. Purple Teaming: What If Red and Blue Teams Work Together?
Traditionally, penetration testers Red Team, attack while defenders Blue Team, defend often separately. Purple Teaming is a new approach where both sides work together during testing to improve security faster.
Example: During a test, the Red Team finds a way to move laterally through a network. The Blue Team watches it in real time and updates their monitoring tools and firewall rules immediately.
Why it matters: It’s a more collaborative and educational method, helping internal teams learn directly from simulated attacks.
3. Continuous & Automated Testing: Is Once-a-Year Still Enough?
With systems changing so quickly (new apps, users, updates), one-time tests aren’t enough. Businesses are now moving toward Continuous Penetration Testing using automation and integration with their CI/CD pipelines.
Example: A company links penetration testing tools with its software development platform. Each time the code is updated, the tool runs scans and alerts the team of new risks before pushing to production.
Why it matters: This shift catches vulnerabilities early, saves time, and lowers long-term risk.
4. Cloud & API Pentesting: Are the New Attack Surfaces Secure?
With most businesses now in the cloud, new kinds of tests are needed, especially for APIs, containers, and cloud misconfigurations.
Example: A tester discovers that a public API doesn’t have proper authentication. This allows anyone to query sensitive user information, showing how a minor mistake can become a big breach.
Why it matters: APIs and cloud environments are becoming the new front doors for hackers, and they need just as much attention.
5. Security Compliance Demand: Are Regulations Driving More Testing?
Laws like GDPR, HIPAA, PCI-DSS, and ISO 27001 are now pushing companies to prove they’ve tested their systems. In many cases, penetration testing is required by law or contract.
Example: A fintech startup is preparing for PCI-DSS compliance. As part of the audit, they must show a full penetration testing report and remediation steps, or risk failing certification.
Why it matters: Compliance is no longer optional. Security testing has become a business requirement.
So, digital AI world in 2025, advanced penetration testing is smarter, faster, and more integrated than ever. Tools are powered by AI, teams are working together in real time, and testing is becoming a continuous process, not just a once-a-year task.
5 Best Checklist Steps For Beginner-Friendly: How Do You Get Started With Penetration Testing?
You’ve learned the what, why, where, and how of penetration testing. Now the big question: How do you actually begin? If you’re a small business owner, IT manager, or just security-curious, here’s a simple step-by-step path to help you get started.
Step 1: Understand What You Need to Protect
Start with your assets. What matters most in your system? Common examples include:
- Customer data
- Financial transactions
- Employee credentials
- Cloud servers and APIs
- Company intellectual property
Suggest: Make a quick list of your top 5 digital assets. These will suggest the rest of your decisions.
Step 2: Choose the Right Type of Test
Refer back to the Types of Penetration Testing section (from earlier in the article). Decide what you want to test:
- External web app? Web Application Pentest
- Internal network? Network Pentest
- Cloud services? Cloud Security Pentest
- Physical access? Physical Security Testing
- Employees’ awareness? Social Engineering Test
Suggest: You don’t have to test everything at once. Start small, then expand over time.
Step 3: Pick Your Approach: Black, White, or Gray Box?
Depending on how much access you give the tester, the test will feel more like a real attack or a controlled review:
- Black Box: No knowledge: just like a real hacker.
- White Box: Full access: focuses on depth.
- Gray Box: Limited knowledge: a mix of both.
Beginner-friendly choice: Gray box testing gives a balance between realism and insight.
Step 4: Hire a Certified Penetration Tester
Look for professionals with certifications like:
- CEH (Certified Ethical Hacker)
- OSCP (Offensive Security Certified Professional)
- CREST or GIAC GPEN
Suggest: Ask for sample reports. Make sure the tester explains findings in a way your team can understand and fix.
Step 5: Act on the Findings For Advanced Penetration Testers
A good penetration test ends with a report that:
- Lists vulnerabilities (ranked by risk)
- Shows how they were exploited
- Recommends how to fix them
Suggest: Don’t ignore the report! Prioritize the top risks and assign fixes to your tech team. Retest if needed.
Final Thoughts: Best tools for advanced penetration testing
Advanced penetration testing (APT) isn’t just for big companies, it’s for anyone serious about security facts. As threats evolve, testing must become a regular habit, not just a one-time checklist. If you’re protecting customer data, securing a cloud app, or preparing for compliance, a smart, focused pentest can save your business from disaster.
APT helps find hidden security problems before attackers do. This testing follows five main steps: reconnaissance, scanning, exploitation, post-exploitation, and reporting. It uses tools like Nmap, Burp Suite, Metasploit, and SQLmap to test how easy it is to break into your systems.
There are different types too, like black-box, white-box, gray-box, and even blind testing, where the test team has no inside info.
If you’re a beginner at internet security and start small. Use this guide, ask questions, and build up your online security one step at a time. Because when it comes to cybersecurity, the best attack is one that never happens.
FAQs: Advanced Penetration Testing Steps and Methodology
1. What is penetration testing and why is it important?
Penetration testing (or pentesting) is a security process where professionals simulate real cyberattacks on your system, app, or network to find and fix weaknesses before hackers do. It’s crucial because it helps organizations protect sensitive data, avoid breaches, and meet security compliance standards.
2. Is penetration testing the same as ethical hacking?
Not exactly. Ethical hacking is a broad term that includes many legal hacking activities, while penetration testing is a more focused process that simulates real attacks to test specific weaknesses. Ethical hackers may perform pentests, but not all ethical hacking involves full penetration testing.
3. What are the different types of penetration testing?
There are several types depending on the focus area:
- Network Penetration Testing
- Web Application Testing
- Wireless Testing
- Social Engineering
- Cloud & API Testing
Each test has a specific goal, from checking firewalls to simulating phishing attacks.
4. What are the 5 stages of a penetration test?
A standard penetration test typically includes:
- Planning and Reconnaissance
- Scanning and Enumeration
- Vulnerability Assessment
- Exploitation
- Reporting and Remediation
Each phase ensures a complete and responsible review of vulnerabilities.
5. Who should perform a penetration test?
Penetration tests should be done by certified experts with credentials like OSCP, CEH, or CREST. These professionals have the skills and tools to simulate real attacks safely and legally.
6. How often should a company do penetration testing?
At a minimum, once a year, or after any major system changes, software launches, or security incidents. Some organizations even do continuous penetration testing using automated tools.
7. Is AI changing how penetration testing works?
Yes. Artificial Intelligence (AI) tools now help automate parts of penetration testing, like scanning for vulnerabilities and analyzing large networks. This makes testing faster and more efficient, especially in cloud environments.
8. What industries benefit most from penetration testing?
Any business with sensitive data should consider pentesting. Advanced facts of penetration testing include:
- Healthcare (HIPAA compliance)
- Finance (PCI-DSS audits)
- E-commerce
- SaaS & Cloud Platforms
- Government agencies
So, understanding what a penetration test entails and how it can safeguard your organization against cyber threats. You’ll not only stay one step ahead of malicious actors but also gain valuable insights into strengthening your digital defenses.
